About PowerApp Connectors
A connector is a proxy or a wrapper around an API that allows the underlying service to talk to Microsoft Power Automate, Microsoft Power Apps, and Azure Logic Apps. It provides a way for the users to connect their accounts and leverage a set of prebuilt actions and triggers to build their apps and workflows.Prerequisites
- Azure Subscription
- Azure Active Directory Tenant
- Azure Power Apps Subscription
-
Once of the following roles to the client Azure account:
- Global Administrator
- Cloud Application Administrator
- Application Administrator
- Owner of the service principal
-
The following roles within the Manifest Web Application:
- Security Admin
How to Set-up a PowerApp Connector
Register App in Azure Active Directory
- Sign into the Azure portal
- In the Azure portal, search for and select Azure Active Directory
- Select App registrations
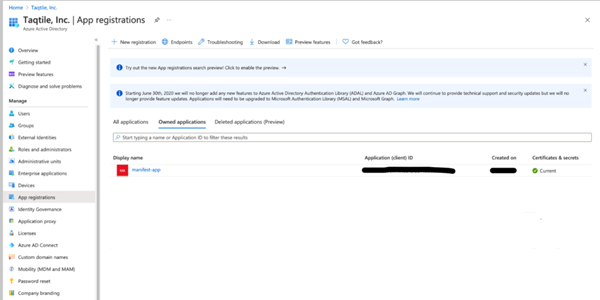
- Select ’+ New Registration’
-
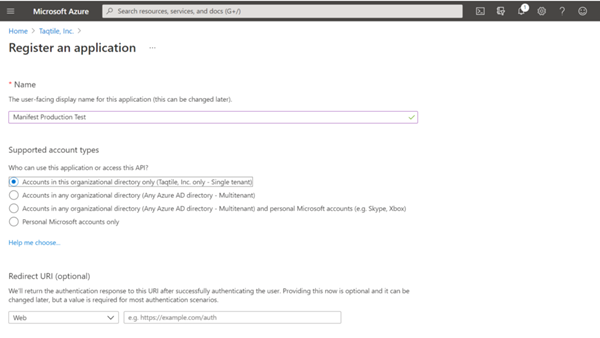
Complete the App registration form:
- Enter the desired user-facing display name, eg. ‘Manifest’
- Choose the scope for application authentication (most single tenant users will select the first option: Support Account types - select ‘Accounts in this organizational directory only’)
- Redirect URI is (optional) - leave blank
- Select Register
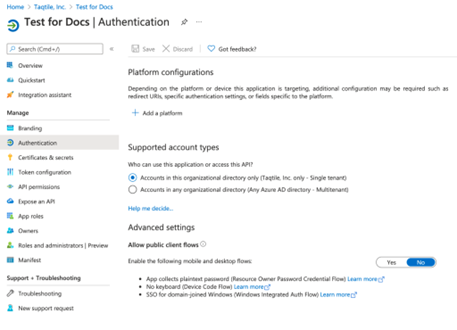
- From the App registration screen, under “Owned applications” select the Manifest app you just created
- Go to the Authentication tab
- Select + Add a platform
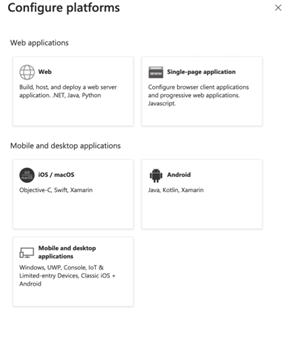
- On the Configure platform select Web
- Enter the redirect URI of the application
- domain.com/rest/dynamics/token
- domain.com/rest/dynamics/auth IMPT! insert your full Manifest domain URL in place of domain.com eg: https://mysubdomain.taqmanifest.com/rest/dynamics/token
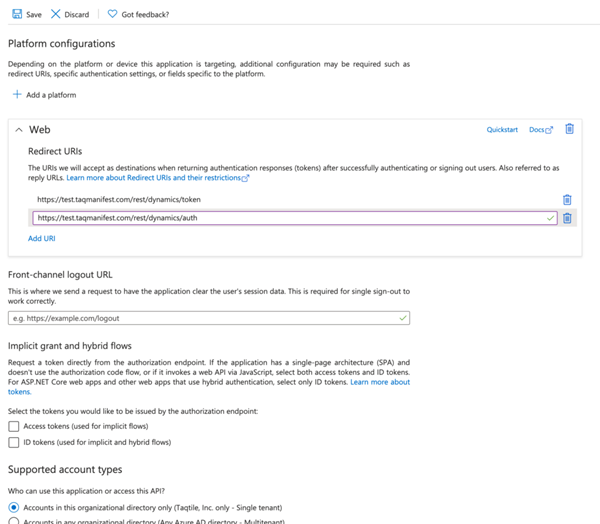
- Go to Certificates + secrets tab
-
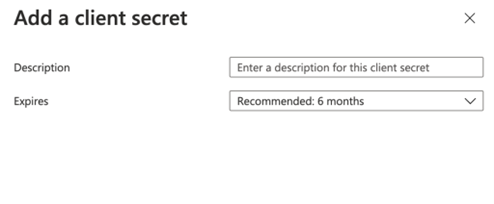
Under Client secrets, select ’+ New Client Secret’ and add a client secret
- Provide a description and expiration and a client secret will be automatically generated
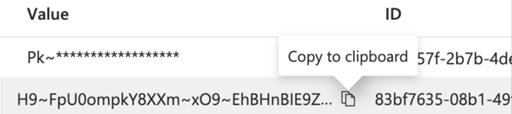
- IMPT! Copy the key once created and save this. You will need this to configure your AD in Manifest. Once you leave this screen you WILL NOTE be able to access this secret value again.
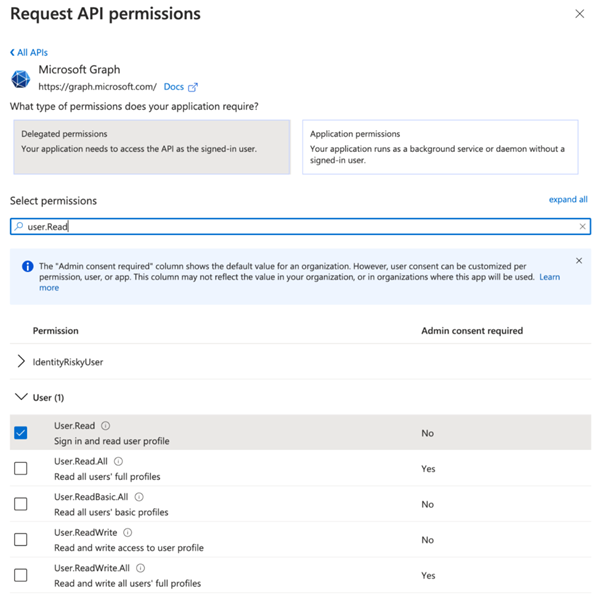
- Go to the ‘API Permissions’ tab
- Select ’+ Add a permission’, The ‘Request API permissions’ window will fly out
- Under Microsoft API’s, select Microsoft Graph. You will be prompted to indicate what type of permissions your application requires.
-
Select Delegated Permissions and search for and then check off the following permissions:
- User.read
- Sites.Manage.All
- Sites.Read.All
- User.Read
- Before logging out, be sure to make note of the following information required to configure your Active Directory in Manifest:
- Application (client) ID: available under App registrations
- Client Secret: create in step 12
- Directory (tenant) ID: available on the Overview tab
Configuring Manifest with your client Azure AD
- Sign into the Manifest Client Portal
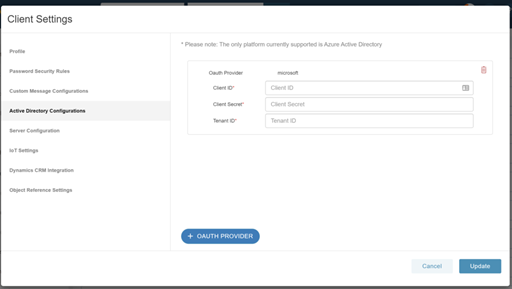
- Select ‘Client Settings’ and go to the Active Directory Configurations tab
- Select ‘+OAUTH PROVIDER’
-
Enter in the following information gathered when adding the Manifest application to your Azure AD tenant:
- Client ID
- Client Secret
- Tenant ID
- Select Update
Install Custom Connector
- Login to Power Apps at https://make.powerapps.com
- Go to the custom connector page

- Go to Custom connector —> Import an Open API file
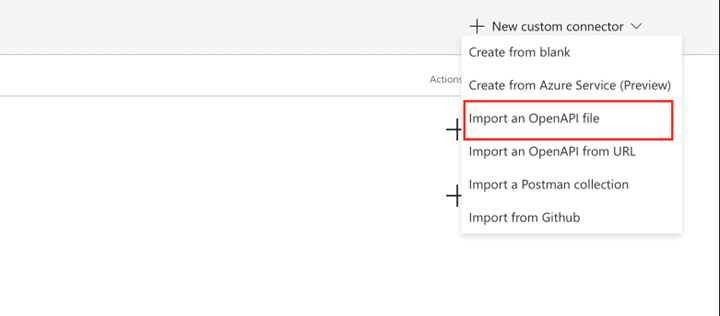
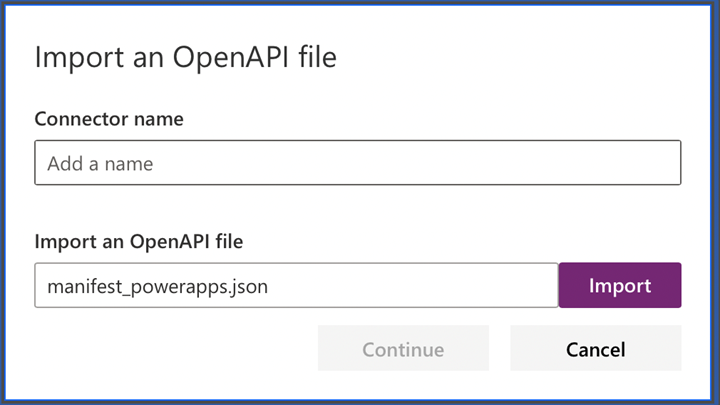
- Download file below and save it into .json format
- Import ‘manifest_powerapps.json’ file
- Change host to Manifest Instance URI e.g. ‘demo.taqmanifest.com’ or ‘apac.taqmanifest.com’

- Go to the next page ‘Security’

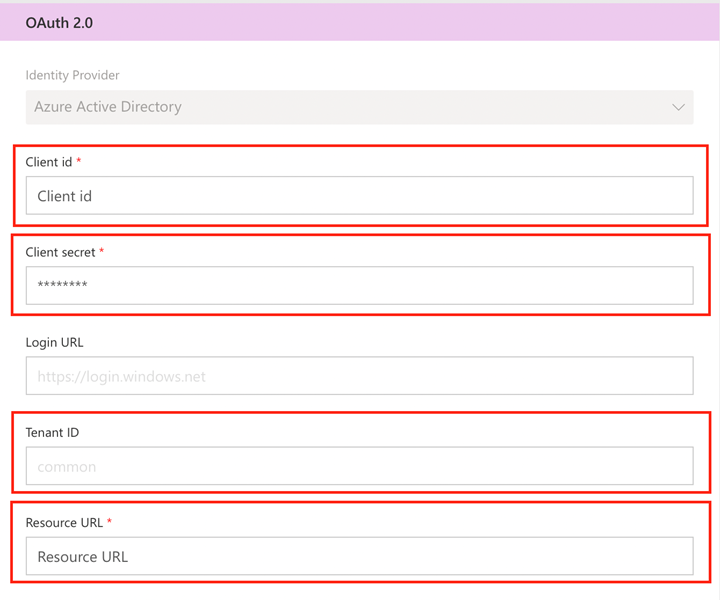
- Set Client ID, Client Secret, Tenant ID to your specific credentials based on your Azure AD Tenant and App registration from the above steps. Set Resource URL to https://graph.microsoft.com/
- Go to the next page ‘Definition’
- Select Create Connector

Create PowerApps Connection
- Go to Custom Connectors Page
- Click Plus button to create connection

- Click Create and then login using Azure AD
- Complete!
